The SparkDev Cyber Security Team.
Author: Joab Kose
Call it whatever you want: Recon, Information Gathering or any other name, but the end goal is that you need to know your enemy before you can make any stupid move. That’s the rule, follow or you’re up to a big shock in security field. So what exactly is reconnaissance and why do we need to perform it? Cybersecurity requires us to understand our target, their motives and what mgettibotivates their drive. This helps a security expert to stay ahead of the enemy and be able to prevent them from harming the assets that we are required to protect. But there’s a problem, I mean there will always be a problem. The adversaries (call them hackers if you want) are getting smarter everyday and as security is tighten, they always come up with new techniques or improve on the existing ones. Their advantage is that, they have access to so much information about they targets and good use of these information sometimes keep them ahead of the game. And sometimes they win! So how do malicious hackers get the information about their target? Well, we give too much information to the world, and sometimes we just care. Sometimes we do care, but we still give it away anyway. We have so much about us outside there, online and offline. We use devices and gadgets that collect data from with or sometimes without our consent. And all these information about our personal lives, work and any information is stored somewhere there; in a datacenter, hard drives or what you would refer to as Cloud (that’s a datacenter somewhere, we just don’t know where it’s). Sometimes I wonder how Google knows me more than I know myself. It can tell that I was at the gym on December 7th, 2018 at 11:23pm. I just allowed it access my information and I just didn’t care. We all do this most of the time. There is much information about individuals, groups, companies and governments on the internet. You just need to know how to find them and the right tools use in order to get them. And hackers are very good at this and once you become their target, they will find everything that they need from you.
Knowing your Target
Knowing the target gives an adversary an easy way of exploiting (hacking) and gaining access to the target. They learn about their weaknesses, ignorances, things they love, where they spend time, people they hangout with, where they work, and many other important information. The main goal is always to find the weakest points that the attacker can take advantage of. Reconnaissance is the is the first stage of any ethical or unethical hacking procedure, and the attacker is always interested in getting a better understanding of the target. The results obtained in this stage play a huge role and determine whether the mission will be successful or not. One needs to take time, use the right tools and techniques in order to this right. Experienced attackers (hackers) have mastered this art and they usually get the job done.
Using the right tools
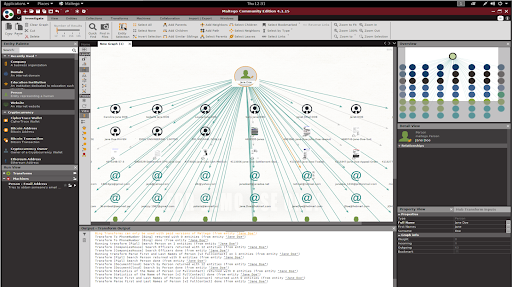
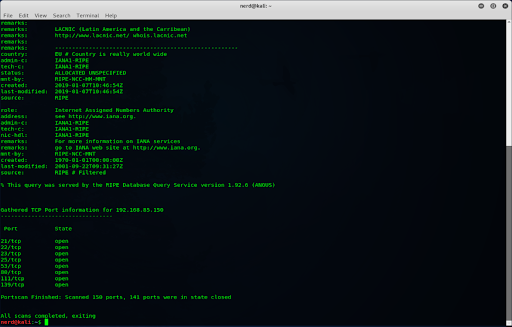
In our project, we go through hands on experience, using some of the amazing reconnaissance tools in trying to understand our target. These tools, when used well give rich information about the target and proper analysis of the obtained result helps the attacker formulate the best move aimed at achieving the end goal; gaining access to the target’s assets. The selection of the tools to be used in Information gathering is determined by the target and the type of attack to be carried. Sometimes, the attackers might deploy some other techniques like social engineering in order to get the information that they want. It’s still part of Recon.